Vulnerability
Vulnerability
|
  90064
90064 |
Authentication Bypass Through Cookie Manipulation

|
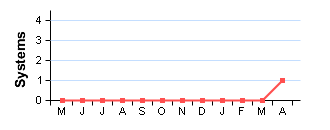
 1 System 1 System |
High Risk |
|---|
| Description | The remote webserver contains a CGI script or web application which uses cookies for authentication in such a way that login bypass is possible by modifying the cookie value. Example cookie values which allow a login are:[For specific url or description click server link below.] |
||||
|---|---|---|---|---|---|
| Solution | Recode your web application source code to use stronger authentication. | ||||
| Category | Application or content flaw. | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 6.8 (Medium) (AV:N/AC:M/Au:N/C:P/I:P/A:N) | |||
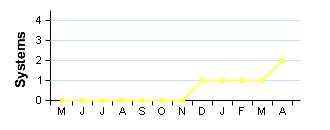
| Systems |
www.example.com (192.168.0.112)

|
|---|
 Vulnerability
Vulnerability
|
  90139
90139 |
Script Allows Arbitrary Command Execution

|
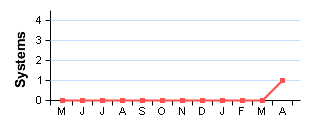
 1 System 1 System |
High Risk |
|---|
| Description | One or more scripts on this host appear to execute commands which can be manipulated by remote users. This flaw may allow arbitrary commands to be executed with the same privileges as the web server. A remote attacker could exploit this flaw to compromise the system. Under some circumstances it may be possible for attacker to elevate the privileges gained though the exploitation of local system flaws. An example that demonstrates this is: [For specific url or description click server link below.] |
||||
|---|---|---|---|---|---|
| Solution | Recode the web application to ensure that unsanitised user supplied input is never included in executable statements. | ||||
| Category | Application or content flaw. | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 7.5 (High) (AV:N/AC:L/Au:N/C:P/I:P/A:P) | |||
| Systems |
www.yourcompany.co.uk (192.168.0.100)


|
|---|
 Vulnerability
Vulnerability
|
  11139
11139 |
Script Appears Vulnerable to SQL Injection

|
 1 System 1 System |
High Risk |
|---|
| Description | One or more scripts on this host appear vulnerable to an SQL injection attack. By requesting the page with parameters containing particular SQL commands, it is possible to force a database level error or otherwise demonstrate that the database is executing user supplied code. This implies that the parameter is being passed to the database without proper input validation. A maliciously crafted parameter could modify the contents of the database, damage it, extract hidden information, allow an attacker to login without a password or allow execution of arbitrary system commands, depending on the type of database. The issue can be demonstrated as follows: [For specific url or description click server link below.] This is simply an example that illustrates the problem, you should fix the underlying injection issue rather than attempting to prevent this exploit from working. Note: Users of Microsoft Internet Explorer may need to disable the 'Show Friendly HTTP Error Messages' option in the Advanced tab of the options dialog in order to see the example properly. |
||||
|---|---|---|---|---|---|
| Solution | Use bound parameters (also known as parameterised commands) and improve input validation in the web application source code. | ||||
| Category | Application or content flaw. | ||||
| References | SQL Injection: Modes of Attack, Defence, and Why It Matters OWASP Top Ten - Injection Flaws Security Considerations for SQL Server: SQL Injection Bobby Tables Guide To Preventing SQL Injection SQL Injection Prevention Cheat Sheet | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 7.5 (High) (AV:N/AC:L/Au:N/C:P/I:P/A:P) | |||
| Systems |
www.yourcompany.co.uk (192.168.0.100)


|
|---|
 Vulnerability
Vulnerability
|
  90085
90085 |
Sensitive Information Leakage

|
 1 System 1 System |
High Risk |
|---|
| Description | This host is leaking information that may be commercially sensitive or help an attacker craft an attack. An example of the information leaked can be found below: [For specific url or description click server link below.] |
||||
|---|---|---|---|---|---|
| Solution | Use a firewall to restrict access to this service. | ||||
| Category | Application or content flaw. | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 5.0 (Medium) (AV:N/AC:L/Au:N/C:P/I:N/A:N) | |||
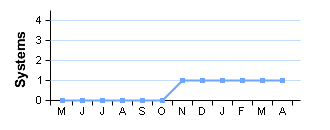
| Systems |
www.example.com (192.168.0.112)

|
|---|
 Vulnerability
Vulnerability
|
  90072
90072 |
Script Allows Arbitrary Redirection

|
 1 System 1 System |
Medium Risk |
|---|
| Description | It is possible to craft a URL which appears to be located on this site, but will redirect users to an arbitrary location. This site could then pose as the legitimate site and prompt users to provide sensitive information. It could also contain any other type of malicious content. The following is an example of a URL which will redirect you to another site:[For specific url or description click server link below.] |
||||
|---|---|---|---|---|---|
| Solution | Recode scripts to allow redirections only to specific locations, for example limit redirections to your own domain. | ||||
| Category | Application or content flaw. | ||||
| References | OWASP Guide: Phishing Phishing: Understanding and Preventing Phishing Attacks Anti-Phishing Technology | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 4.3 (Medium) (AV:N/AC:M/Au:N/C:N/I:P/A:N) | |||
| Systems |
www.yourcompany.co.uk (192.168.0.100)


|
|---|
 Vulnerability
Vulnerability
|
  90111
90111 |
Service Permits Unauthenticated Users to Send Arbitrary Emails

|
 1 System 1 System |
Medium Risk |
|---|
| Description | A service on the remote host appears to allow unauthenticated users to send emails containing arbitrary content. This service might be exploited by a remote attacker to conceal their identity whilst performing activities such as spamming, phishing and fraud. The issue can be demonstrated as follows: [For specific url or description click server link below.] Note: This vulnerability may be a false positive as we do not attempt to send arbitrary messages in order to avoid the possibility of crashing the service. |
||||
|---|---|---|---|---|---|
| Solution | Restrict the service to authenticated users, restrict the allowed recipient email addresses or prevent users from controlling the email's content. Implementing a captcha mechanism could help prevent the attacker from automating their activities. | ||||
| Category | Application or content flaw. | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 0.0 (Low) (AV:N/AC:L/Au:N/C:N/I:N/A:N) | |||
| Systems |
www.yourcompany.co.uk (192.168.0.100)


|
|---|
 Vulnerability
Vulnerability
|
  90110
90110 |
Weak or Ineffective Authentication Mechanism

|
 1 System 1 System |
Medium Risk |
|---|
| Description | The remote server attempts to protect content through a mechanism which is ineffective, or can be trivially circumvented. The issue can be demonstrated as follows:[For specific url or description click server link below.] |
||||
|---|---|---|---|---|---|
| Solution | Recode your application to use a stronger authentication mechanism. | ||||
| Category | Application or content flaw. | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 6.4 (Medium) (AV:N/AC:L/Au:N/C:P/I:P/A:N) | |||
| Systems |
www.your_company.nl (192.168.0.103)


|
|---|
 Vulnerability
Vulnerability
|
  90091
90091 |
XPath Injection

|
 1 System 1 System |
Medium Risk |
|---|
| Description | One or more scripts on this host appear vulnerable to XPath injection attacks. By requesting a page with parameters containing particular XPath elements, it is possible to force an XPath error or otherwise demonstrate that the user supplied code is being interpreted as XPath statements. This implies that a parameter is being passed to an XPath interpreter without proper input validation. A maliciously crafted parameter might be able to extract hidden information, bypass login requirements or even perform code execution depending on the XPath parser used. The issue can be demonstrated as follows: [For specific url or description click server link below.] This is simply an example that illustrates the problem, you should fix the underlying injection issue rather than attempting to prevent this exploit from working. |
||||
|---|---|---|---|---|---|
| Solution | Perform input validation within the web application and utilise query parameterisation where supported by the XPath parser. | ||||
| Category | Application or content flaw. | ||||
| References | XPath Injection - Threat Classification | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 6.8 (Medium) (AV:N/AC:M/Au:N/C:P/I:P/A:P) | |||
| Systems |
www.example.com (192.168.0.112)

|
|---|
 Vulnerability
Vulnerability
|
  10815
10815 |
Cross-Site Scripting |
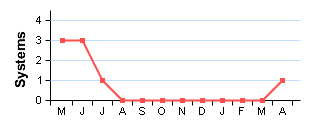
 2 Systems 2 Systems |
Medium Risk |
|---|
| Description | This system is running a web server or web application which is vulnerable to Cross-Site Scripting (XSS) attacks. Certain pages include user-supplied input in the response and HTML special characters are not escaped. An attacker could use this to inject malicious JavaScript or HTML code, which will run at the same trust level as the server. This may enable them to steal session cookies, form details, etc. An example that demonstrates this is: [For specific url or description click server link below.] Note: This vulnerability must be addressed server-side. Adding JavaScript (client-side) validation on form fields does not offer any protection against Cross-Site Scripting or other attacks. |
||||
|---|---|---|---|---|---|
| Solution | Recode your web application to ensure all user supplied input is escaped when displayed, or contact your web application vendor for a patch. Any JavaScript-based fix will not be effective. | ||||
| Category | Application or content flaw. | ||||
| References | CERT Advisory CA-2000-02 XSS Anatomy PHP htmlspecialchars Quoting Function How To: Prevent Cross-Site Scripting in ASP.NET OWASP XSS Prevention Cheat Sheet | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 4.3 (Medium) (AV:N/AC:M/Au:N/C:N/I:P/A:N) | |||
| Systems |
www.your_company.nl (192.168.0.103)


|
www.yourcompany.net (192.168.0.102)
 [Dec 2014]
[Dec 2014]
|
|---|---|---|
 Vulnerability
Vulnerability
|
  11229
11229 |
Script Calling phpinfo() Detected

|
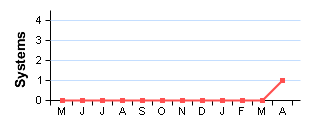
 1 System 1 System |
Low Risk |
|---|
| Description | This system has a PHP script that calls phpinfo(). This function displays a significant amount of system and configuration information. A remote attacker could use this for reconnaissance. An example of a URL you can use to exploit this is: [For specific url or description click server link below.] |
||||
|---|---|---|---|---|---|
| Solution | Remove this script, or protect it with some kind of authentication. | ||||
| Category | Application or content flaw. | ||||
| References | phpinfo documentation | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 5.0 (Medium) (AV:N/AC:L/Au:N/C:P/I:N/A:N) | |||
| Deadline | 13 January 2015 | ||||
| Systems |
apollo.example.com (192.168.0.81)
 [Nov 2014]
[Nov 2014]
|
|---|