Criticality:  System Reference: YC100
System Reference: YC100
 System Reference: YC100
System Reference: YC100
| Groups and Contacts | |||
|---|---|---|---|
| Region | EMEA | Business | janebloggs@yourcompany.com |
| Platform | Unix | Technical | johndoe@yoursecurity.co.uk |
 Scan Information
Scan Information
|
|
|---|---|
| Scan Type | Enterprise |
| Started at | 13-Apr-15 11:54 |
| Finished at | 13-Apr-15 12:54 |
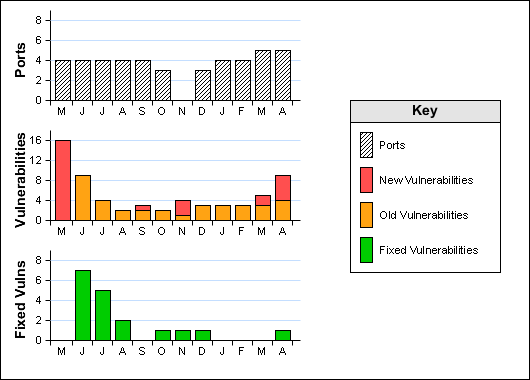
Ports: 5 (High:0 Low:5)
| Port | Protocol | Service | Details | ||
|---|---|---|---|---|---|
| 25 | tcp | smtp | ESMTP Server (Microsoft Exchange Internet Mail Service 5.5.2653.13) ready | ||
| 80 | tcp | http | Apache/1.3.26 (Unix) Debian GNU/Linux | ||
| 110 | tcp | pop3 | +OK Qpopper (version 4.0.6) starting. | ||
| 443 | tcp | https | Microsoft-IIS 5.0 | ||
| 0 | icmp | echo reply | Response Received |
Vulnerabilities: 9 (High:3 Medium:3 Low:3)
| Vulnerability | 90109 | Possible Compromise

|
High Risk |
|---|
| Description | Suspicious content or behaviour from the remote host indicates that it may have been compromised by a virus or remote attacker.The remote host appears to have been compromised. http://www.yourcompany.co.uk/forums contains a large number of suspicious links in its HTML source code. black.hats.cn/phe/Phentermine-without-doctor's-approval.html black.hats.cn/pharmacy/Percocet.html black.hats.cn/phe/Phentermine-and-atkins-diet.html black.hats.cn/via/Free-viagra-prescription.html |
||||
|---|---|---|---|---|---|
| Solution | Consider restoring the host from trusted media. | ||||
| Category | N/A | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 10.0 (High) (AV:N/AC:L/Au:N/C:C/I:C/A:C) | |||
| First Found | 13 April 2015 | Port | 443/tcp | Last 6 Assessments | 





|
| Vulnerability | 90139 | Script Allows Arbitrary Command Execution

|
High Risk |
|---|
| Description | One or more scripts on this host appear to execute commands which can be manipulated by remote users. This flaw may allow arbitrary commands to be executed with the same privileges as the web server. A remote attacker could exploit this flaw to compromise the system. Under some circumstances it may be possible for attacker to elevate the privileges gained though the exploitation of local system flaws. An example that demonstrates this is: http://www.yourcompany.co.uk/downloadreport.php?filename=ls -1| . .. cn.crt cn.csr cn.key 12605.out 12632.out 15550.out 19429.out 19430.out |
||||
|---|---|---|---|---|---|
| Solution | Recode the web application to ensure that unsanitised user supplied input is never included in executable statements. | ||||
| Category | Application or content flaw. | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 7.5 (High) (AV:N/AC:L/Au:N/C:P/I:P/A:P) | |||
| First Found | 13 April 2015 | Port | 80/tcp | Last 6 Assessments | 





|
| Vulnerability | 11139 | Script Appears Vulnerable to SQL Injection

|
High Risk |
|---|
| Description | One or more scripts on this host appear vulnerable to an SQL injection attack. By requesting the page with parameters containing particular SQL commands, it is possible to force a database level error or otherwise demonstrate that the database is executing user supplied code. This implies that the parameter is being passed to the database without proper input validation. A maliciously crafted parameter could modify the contents of the database, damage it, extract hidden information, allow an attacker to login without a password or allow execution of arbitrary system commands, depending on the type of database. The issue can be demonstrated as follows: http://www.yourcompany.co.uk/testimonials/customers.php?custid=convert(Int,@@version) Syntax error converting the nvarchar value 'Microsoft SQL Server 2000 - 8.00.2123 (Intel X86) May 3 2006 22:15:30 Copyright (c) 1988-2003 Microsoft Corporation Enterprise Edition on Windows NT 5.0 (Build 2195: Service Pack 4) ' to a column of data type int. This is simply an example that illustrates the problem, you should fix the underlying injection issue rather than attempting to prevent this exploit from working. Note: Users of Microsoft Internet Explorer may need to disable the 'Show Friendly HTTP Error Messages' option in the Advanced tab of the options dialog in order to see the example properly. |
||||
|---|---|---|---|---|---|
| Solution | Use bound parameters (also known as parameterised commands) and improve input validation in the web application source code. | ||||
| Category | Application or content flaw. | ||||
| References | Security Considerations for SQL Server: SQL Injection Bobby Tables Guide To Preventing SQL Injection OWASP Top Ten - Injection Flaws SQL Injection: Modes of Attack, Defence, and Why It Matters SQL Injection Prevention Cheat Sheet | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 7.5 (High) (AV:N/AC:L/Au:N/C:P/I:P/A:P) | |||
| First Found | 13 May 2014 | Port | 443/tcp | Last 6 Assessments | 





|
| Vulnerability | 11137 | Apache < 1.3.27 Multiple Vulnerabilities | Medium Risk |
|---|
| Description | This system is running a vulnerable version of Apache, according to its banner. There is a cross-site scripting vulnerability through the Host: header, if UseCanonicalName is Off. Exploitation is only possible where wildcard DNS is used. There is also a buffer overrun in the ApacheBench module - if this is enabled, it may allow arbitrary code execution. A further vulnerability exists in the shared memory scoreboard, but this is only exploitable by a local user. | ||||
|---|---|---|---|---|---|
| Solution | Upgrade to an unaffected version, or apply a patch. Workaround : Set UseCanonicalName to On and disable ApacheBench |
||||
| Category | Hosting or infrastructure flaw. | ||||
| References | Apache 1.3 Changelog | ||||
| CVE References | CVE-2002-0839 | CVSS2 7.2 (High) (AV:L/AC:L/Au:N/C:C/I:C/A:C) | |||
| CVE-2002-0840 | CVSS2 6.8 (Medium) (AV:N/AC:M/Au:N/C:P/I:P/A:P) | ||||
| CVE-2002-0843 | CVSS2 7.5 (High) (AV:N/AC:L/Au:N/C:P/I:P/A:P) | ||||
| First Found | 13 November 2014 | Port | 80/tcp | Last 6 Assessments | 





|
| Vulnerability | 90072 | Script Allows Arbitrary Redirection

|
Medium Risk |
|---|
| Description | It is possible to craft a URL which appears to be located on this site, but will redirect users to an arbitrary location. This site could then pose as the legitimate site and prompt users to provide sensitive information. It could also contain any other type of malicious content. The following is an example of a URL which will redirect you to another site:http://www.yourcompany.co.uk/redirect.php?url=http://www.example.com |
||||
|---|---|---|---|---|---|
| Solution | Recode scripts to allow redirections only to specific locations, for example limit redirections to your own domain. | ||||
| Category | Application or content flaw. | ||||
| References | Phishing: Understanding and Preventing Phishing Attacks Anti-Phishing Technology OWASP Guide: Phishing | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 4.3 (Medium) (AV:N/AC:M/Au:N/C:N/I:P/A:N) | |||
| First Found | 13 April 2015 | Port | 443/tcp | Last 6 Assessments | 





|
| Vulnerability | 90111 | Service Permits Unauthenticated Users to Send Arbitrary Emails

|
Medium Risk |
|---|
| Description | A service on the remote host appears to allow unauthenticated users to send emails containing arbitrary content. This service might be exploited by a remote attacker to conceal their identity whilst performing activities such as spamming, phishing and fraud. The issue can be demonstrated as follows: http://www.yourcompany.co.uk/referafriend.asp appears to allow emails to be sent to arbitrary addresses containing the attackers subject and body text. Note: This vulnerability may be a false positive as we do not attempt to send arbitrary messages in order to avoid the possibility of crashing the service. |
||||
|---|---|---|---|---|---|
| Solution | Restrict the service to authenticated users, restrict the allowed recipient email addresses or prevent users from controlling the email's content. Implementing a captcha mechanism could help prevent the attacker from automating their activities. | ||||
| Category | Application or content flaw. | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 0.0 (Low) (AV:N/AC:L/Au:N/C:N/I:N/A:N) | |||
| First Found | 13 April 2015 | Port | 80/tcp | Last 6 Assessments | 





|
| Vulnerability | 11915 | Apache < 1.3.29 Multiple Local Flaws | Low Risk |
|---|
| Description | This system is running a vulnerable version of Apache, according to its banner. This version contains buffer overruns in mod_alias and mod_rewrite. A local user could exploit these to escalate their privileges. | ||||
|---|---|---|---|---|---|
| Solution | Upgrade to an unaffected version, or apply a patch. | ||||
| References | Bugtraq Apache 1.3 Changelog | ||||
| CVE Reference | CVE-2003-0542 | CVSS2 7.2 (High) (AV:L/AC:L/Au:N/C:C/I:C/A:C) | |||
| First Found | 13 November 2014 | Port | 80/tcp | Last 6 Assessments | 





|
| Vulnerability | 10759 | Private IP Address Leakage | Low Risk |
|---|
| Description | This system exposes its RFC 1918 private IP address. This is the internal IP address of the system, that would usually be masked by a proxy or NAT firewall. This information may be useful to an attacker trying to remotely map your network or prepare an attack. The private IP address is:10.0.0.100 |
||||
|---|---|---|---|---|---|
| Solution | Update your web server configuration. For IIS, issue "adsutil set w3svc/UseHostName True" and restart. On Apache, ensure that ServerName in httpd.conf is set to a hostname. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| References | Bugtraq ID 1499 Microsoft Knowledge Base Q218180 RFC 1918 | ||||
| CVE Reference | CVE-2000-0649 | CVSS2 2.6 (Low) (AV:N/AC:H/Au:N/C:P/I:N/A:N) | |||
| First Found | 13 March 2015 | Port | 80/tcp, 443/tcp | Last 6 Assessments | 





|
| Vulnerability | 11213 | TRACE and/or TRACK Methods Enabled | Low Risk |
|---|
| Description | This system supports the HTTP TRACE and/or TRACK methods. These increase the exploitability of any cross-site scripting vulnerabilities that may exist in your site. As they are primarily intended for debugging, they can be turned off without reduction of service. | ||||
|---|---|---|---|---|---|
| Solution | Disable these methods on production servers. Microsoft IIS 6 and IIS 7: Use the URLScan Security tool Microsoft IIS 5: Use the IIS Lockdown tool Apache httpd: Use mod_rewrite to redirect unallowed verbs to the forbidden target, or with newer versions use the configuration option 'TraceEnable off'. |
||||
| Category | Hosting or infrastructure flaw. | ||||
| References | US-CERT VU#867593 UrlScan Security Tool IIS Lockdown Tool Apache TraceEnable Directive | ||||
| CVE References | CVE-2003-1567 | CVSS2 2.6 (Low) (AV:N/AC:H/Au:N/C:P/I:N/A:N) | |||
| CVE-2004-2320 | CVSS2 2.6 (Low) (AV:N/AC:H/Au:N/C:P/I:N/A:N) | ||||
| CVE-2010-0386 | CVSS2 2.6 (Low) (AV:N/AC:H/Au:N/C:P/I:N/A:N) | ||||
| First Found | 13 May 2014 | Port | 80/tcp | Last 6 Assessments | 





|
Vulnerabilities Fixed Since the Last Scan: 1 (High:0 Medium:0 Low:1)
| Vulnerability | 12279 | QPopper <= 4.0.5 User Names Information Leakage | Low Risk |
|---|
| Description | According to its banner, this host is running a vulnerable version of QPopper. These versions return a different error message on failed login, depending on whether the user name exists. An attacker can use this to enumerate users - the starting point for a password guessing attack. | ||||
|---|---|---|---|---|---|
| Solution | No patch is currently available. You must either accept this risk or choose another POP3 server. | ||||
| References | Bugtraq ID 7110 | ||||
| CVE Reference | CVE-2001-1068 | CVSS2 5.0 (Medium) (AV:N/AC:L/Au:N/C:P/I:N/A:N) | |||
| First Found | 13 March 2015 | Port | 110/tcp | Last 6 Assessments | 





|
Historical Information