Criticality: 

| Groups and Contacts | |||
|---|---|---|---|
| Region | US | Business | janebloggs@yourcompany.com |
| Platform | Unix | Technical | johndoe@yoursecurity.co.uk |
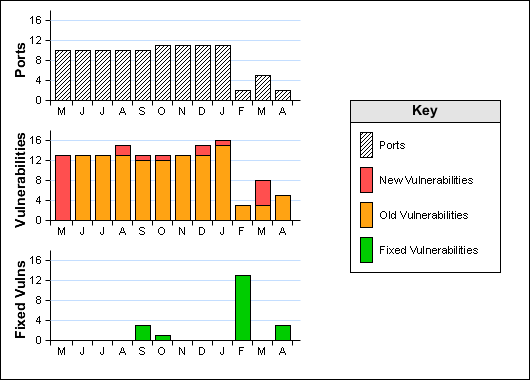
 Scan Information
Scan Information
|
|
|---|---|
| Scan Type | Enterprise |
| Started at | 13-Apr-15 11:54 |
| Finished at | 13-Apr-15 12:54 |
Ports: 2 (High:0 Low:2)
| Port | Protocol | Service | Details | ||
|---|---|---|---|---|---|
| 100 | tcp | unknown | Apache | ||
| 200 | tcp | unknown | SSH-2.0-OpenSSH_2.9p2 |
Ports Closed Since the Last Scan: 3 (High:3 Low:0)
| Port | Protocol | Service | Details | ||
|---|---|---|---|---|---|
| 135 | tcp | msrpc | No banner found | ||
| 137 | tcp | netbios-ns | 8 names found | ||
| 139 | tcp | netbios-ssn | Close Immediately with TCP RST |
Vulnerabilities: 5 (High:1 Medium:2 Low:2)
| Vulnerability | 10882 | SSH Protocol Version 1 Enabled | High Risk |
|---|
| Description | This system is running an SSH service with SSH protocol version 1 enabled. This version of the protocols is not completely cryptographically secure. A passive eavesdropper could use these weaknesses to extract information such as the lengths of passwords and commands. | ||||
|---|---|---|---|---|---|
| Solution | Configure your SSH service to only use protocol version 2. For OpenSSH, set the 'Protocol' option to '2'. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| References | US-CERT VU#596827 OSVDB ID 2116 | ||||
| CVE References | CVE-2001-0361 | CVSS2 4.0 (Medium) (AV:N/AC:H/Au:N/C:P/I:P/A:N) | |||
| CVE-2001-0572 | CVSS2 7.5 (High) (AV:N/AC:L/Au:N/C:P/I:P/A:P) | ||||
| CVE-2001-1473 | CVSS2 7.5 (High) (AV:N/AC:L/Au:N/C:P/I:P/A:P) | ||||
| First Found | 13 January 2015 | Port | 22/tcp | Last 6 Assessments | 





|
| Vulnerability | 10815 | Cross-Site Scripting | Medium Risk |
|---|
| Description | This system is running a web server or web application which is vulnerable to Cross-Site Scripting (XSS) attacks. Certain pages include user-supplied input in the response and HTML special characters are not escaped. An attacker could use this to inject malicious JavaScript or HTML code, which will run at the same trust level as the server. This may enable them to steal session cookies, form details, etc. An example that demonstrates this is: https://192.168.0.102/x/<script>alert("vulnerable!")</script>
Note: This vulnerability must be addressed server-side. Adding JavaScript (client-side) validation on form fields does not offer any protection against Cross-Site Scripting or other attacks. |
||||
|---|---|---|---|---|---|
| Solution | Recode your web application to ensure all user supplied input is escaped when displayed, or contact your web application vendor for a patch. Any JavaScript-based fix will not be effective. | ||||
| Category | Application or content flaw. | ||||
| References | How To: Prevent Cross-Site Scripting in ASP.NET OWASP XSS Prevention Cheat Sheet PHP htmlspecialchars Quoting Function CERT Advisory CA-2000-02 XSS Anatomy | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 4.3 (Medium) (AV:N/AC:M/Au:N/C:N/I:P/A:N) | |||
| First Found | 13 December 2014 | Port | 80/tcp | Last 6 Assessments | 





|
| Vulnerability | 10539 | Globally Useable Name Server | Medium Risk |
|---|
| Description | This system is running a name server that allows any system on the Internet to perform recursive queries and resolve third-party domain names. An attacker could use this to extract information about your name lookup patterns, and may be able to perform DNS cache poisoning attacks. | ||||
|---|---|---|---|---|---|
| Solution | Restrict recursive queries to trusted addresses. For servers running BIND, use the allow-recursion or allow-query directives. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| References | Disabling recursion in BIND Securing Windows Server 2003 Domain Controllers | ||||
| CVE Reference | CVE-1999-0024 | CVSS2 5.0 (Medium) (AV:N/AC:L/Au:N/C:N/I:P/A:N) | |||
| First Found | 13 May 2014 | Port | 53/udp | Last 6 Assessments | 





|
| Vulnerability | 12217 | DNS Cache Snooping | Low Risk |
|---|
| Description | This system is running a DNS server that accepts queries from any address (although recursive queries may be disabled). The name server responds differently for domains that have recently been looked-up. An attacker could use this to determine if certain sites have been visited by users of this nameserver. | ||||
|---|---|---|---|---|---|
| Solution | Restrict access to DNS caches to local users. For Bind, use the "AllowQuery" directive. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| References | What is DNS Cache Snooping? DNS Cache Snooping | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 0.0 (Low) (AV:N/AC:M/Au:N/C:N/I:N/A:N) | |||
| First Found | 13 March 2015 | Port | 53/udp | Last 6 Assessments | 





|
| Vulnerability | 11213 | TRACE and/or TRACK Methods Enabled | Low Risk |
|---|
| Description | This system supports the HTTP TRACE and/or TRACK methods. These increase the exploitability of any cross-site scripting vulnerabilities that may exist in your site. As they are primarily intended for debugging, they can be turned off without reduction of service. | ||||
|---|---|---|---|---|---|
| Solution | Disable these methods on production servers. Microsoft IIS 6 and IIS 7: Use the URLScan Security tool Microsoft IIS 5: Use the IIS Lockdown tool Apache httpd: Use mod_rewrite to redirect unallowed verbs to the forbidden target, or with newer versions use the configuration option 'TraceEnable off'. |
||||
| Category | Hosting or infrastructure flaw. | ||||
| References | US-CERT VU#867593 UrlScan Security Tool IIS Lockdown Tool Apache TraceEnable Directive | ||||
| CVE References | CVE-2003-1567 | CVSS2 2.6 (Low) (AV:N/AC:H/Au:N/C:P/I:N/A:N) | |||
| CVE-2004-2320 | CVSS2 2.6 (Low) (AV:N/AC:H/Au:N/C:P/I:N/A:N) | ||||
| CVE-2010-0386 | CVSS2 2.6 (Low) (AV:N/AC:H/Au:N/C:P/I:N/A:N) | ||||
| First Found | 13 December 2014 | Port | 100/tcp | Last 6 Assessments | 





|
Vulnerabilities Fixed Since the Last Scan: 3 (High:1 Medium:2 Low:0)
| Vulnerability | 90027 | High Risk Ports Open | High Risk |
|---|
| Description | The following high risk ports are open: PORT SERVICE 135/tcp msrpc 137/tcp netbios-ns 139/tcp netbios-ssn Note: Even if the ports are immediately closed after being opened, this is still a security risk as packets are reaching the destination host. It is recommended to completely drop packets from untrusted sources instead. |
||||
|---|---|---|---|---|---|
| Solution | Ensure that the ports are filtered by your router or firewall or close the ports on the affected systems. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 6.4 (Medium) (AV:N/AC:L/Au:N/C:P/I:P/A:N) | |||
| First Found | 13 May 2014 | Port | general | Last 6 Assessments | 





|
| Vulnerability | 11793 | Apache < 1.3.28 Multiple flaws | Medium Risk |
|---|
| Description | According to its banner, this web server is running a version of Apache older than 1.3.28. This version contains fixes for multiple minor denial of service flaws. Although these are not exploitable in all configurations, it is recommended that you upgrade to the latest version. | ||||
|---|---|---|---|---|---|
| Solution | Upgrade to an unaffected version. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| References | Apache 1.3 Changelog | ||||
| CVE References | CVE-2002-0061 | CVSS2 7.5 (High) (AV:N/AC:L/Au:N/C:P/I:P/A:P) | |||
| CVE-2003-0460 | CVSS2 5.0 (Medium) (AV:N/AC:L/Au:N/C:N/I:N/A:P) | ||||
| First Found | 13 March 2015 | Port | No information available | Last 6 Assessments | 





|
| Vulnerability | 10736 | DCE Services Enumeration | Medium Risk |
|---|
| Description | It is possible for any remote user to connect to port 135 on this host and enumerate the available DCE services. The information leaked is relatively low risk, although an attacker could use it to focus their strategy. However, the vulnerability is more worrying because it shows that Windows file sharing (NetBIOS) is accessible over the internet, which is considered unwise. |
||||
|---|---|---|---|---|---|
| Solution | Use a firewall to restrict access to Windows file sharing ports to trusted addresses. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 5.0 (Medium) (AV:N/AC:L/Au:N/C:P/I:N/A:N) | |||
| First Found | 13 March 2015 | Port | 135/tcp | Last 6 Assessments | 





|
Historical Information