Criticality:  System Reference: YC103
System Reference: YC103
 System Reference: YC103
System Reference: YC103
| Groups and Contacts | |||
|---|---|---|---|
| Region | EMEA | Business | janebloggs@yourcompany.com |
| Platform | Microsoft | ||
 Scan Information
Scan Information
|
|
|---|---|
| Scan Type | Enterprise |
| Started at | 13-Apr-15 11:54 |
| Finished at | 13-Apr-15 12:54 |
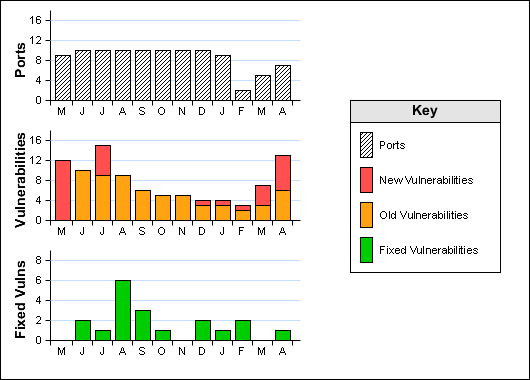
Ports: 7 (High:0 Low:7)
| Port | Protocol | Service | Details | ||
|---|---|---|---|---|---|
| 53 | tcp | domain | Closed Immediately with TCP FIN | ||
| 80 | tcp | http | Microsoft-IIS 5.0 | ||

|
161 | tcp | snmp | uptime 278411121 centiseconds | |
| 443 | tcp | https | Microsoft-IIS 5.0 | ||
| 53 | udp | dns | Response Received | ||

|
0 | icmp | echo reply | Response Received | |

|
14 | icmp | timestamp reply | Timestamp is 12:46:03 |
Ports Closed Since the Last Scan: 1 (High:0 Low:1)
| Port | Protocol | Service | Details | ||
|---|---|---|---|---|---|
| 3053 | udp | dsom-server | Response received |
Vulnerabilities: 13 (High:5 Medium:5 Low:3)
| Vulnerability | 90052 | Administration Interface with Weak Password

|
High Risk |
|---|
| Description | This host is exposing an administration interface to the Internet with a default or easily guessable password. This allows a remote attacker full access to modify settings or content. The login details are: http://www.your_company.nl/tightcms/login.aspx Username: builtin Password: builtin |
||||
|---|---|---|---|---|---|
| Solution | Set a stronger password and/or ensure this interface is not accessible from the Internet. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| CVE Reference | CVE-1999-0508 | CVSS2 7.5 (High) (AV:N/AC:L/Au:N/C:P/I:P/A:P) | |||
| First Found | 13 April 2015 | Port | 443/tcp | Last 6 Assessments | 





|
| Vulnerability | 90027 | High Risk Ports Open

|
High Risk |
|---|
| Description | The following high risk ports are open: PORT SERVICE 161/udp snmp Note: Even if the ports are immediately closed after being opened, this is still a security risk as packets are reaching the destination host. It is recommended to completely drop packets from untrusted sources instead. |
||||
|---|---|---|---|---|---|
| Solution | Ensure that the ports are filtered by your router or firewall or close the ports on the affected systems. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 6.4 (Medium) (AV:N/AC:L/Au:N/C:P/I:P/A:N) | |||
| First Found | 13 May 2014 | Port | 161/tcp | Last 6 Assessments | 





|
| Vulnerability | 10993 | IIS ASP.NET Application Trace Enabled

|
High Risk |
|---|
| Description | This web server has an ASP.NET application running with application tracing enabled. This allows an attacker to view detailed information on recent HTTP requests. Sensitive information revealed includes physical paths and even session IDs. An example URL you can use to exploit this is: http://www.your_company.nl/recruitment/apply/trace.axd This was found to reveal sensitive information about users. For example: Firstname: John Lastname: Smith Previous Employer: Widgets Corporation Tertiary Education: University of Wallamaloo Gender: Male DOB: 1/1/1985 postcode: 2444 country Australia state NSW street 134 Dribble Creek Road mobile 0403453656 email jsmith@private.com.au |
||||
|---|---|---|---|---|---|
| Solution | Set 'trace enabled=false' in web.config | ||||
| Category | Hosting or infrastructure flaw. | ||||
| References | ASP.Net Tracing Overview How to: Enable Tracing for an ASP.NET Application Tracing How to: Enable Tracing for an ASP.NET Page | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 5.0 (Medium) (AV:N/AC:L/Au:N/C:P/I:N/A:N) | |||
| First Found | 13 April 2015 | Port | 80/tcp,443/tcp | Last 6 Assessments | 





|
| Vulnerability | 11424 | IIS WebDAV Buffer Overrun | High Risk |
|---|
| Description | This system is an IIS server running WebDAV. This may be vulnerable to a buffer overrun when a malicious WebDAV request is sent. When running on an unpatched Windows NT4, Windows 2000, or Windows XP; an attacker could use this to crash the service or take control of the system. Note: This may be a false positive as it is not possible to determine remotely if the patch has been applied. |
||||
|---|---|---|---|---|---|
| Solution | Apply the patch from Microsoft. In addition we suggest you edit registry to disable WebDAV, following these instructions. If you do not disable WebDAV then this vulnerability will continue appearing until you stoplist it. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| References | Microsoft Security Bulletin MS03-007 Microsoft Knowledge Base Q241520 CERT Advisory CA-2003-09 | ||||
| CVE Reference | CVE-2003-0109 | CVSS2 7.5 (High) (AV:N/AC:L/Au:N/C:P/I:P/A:P) | |||
| First Found | 13 May 2014 | Port | 80/tcp | Last 6 Assessments | 





|
| Vulnerability | 10264 | SNMP Default Community Names | High Risk |
|---|
| Description | This system is running an SNMP agent which uses an easily guessable community string. This enables an attacker to extract a large amount of useful information. If a writeable community string is guessable, an attacker could make configuration changes to the server. Here is a sample of the information that can be extracted: host.hrSWRun.hrSWRunTable.hrSWRunEntry.hrSWRunName.1 = "System Idle Process" host.hrSWRun.hrSWRunTable.hrSWRunEntry.hrSWRunName.8 = "System" host.hrSWRun.hrSWRunTable.hrSWRunEntry.hrSWRunName.168 = "SMSS.EXE" host.hrSWRun.hrSWRunTable.hrSWRunEntry.hrSWRunName.192 = "CSRSS.EXE" host.hrSWRun.hrSWRunTable.hrSWRunEntry.hrSWRunName.212 = "WINLOGON.EXE" host.hrSWRun.hrSWRunTable.hrSWRunEntry.hrSWRunName.240 = "SERVICES.EXE" |
||||
|---|---|---|---|---|---|
| Solution | Disable SNMP, or change the community string to something unguessable. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| CVE References | CVE-1999-0186 | CVSS2 10.0 (High) (AV:N/AC:L/Au:N/C:C/I:C/A:C) | |||
| CVE-1999-0254 | CVSS2 10.0 (High) (AV:N/AC:L/Au:N/C:C/I:C/A:C) | ||||
| CVE-1999-0516 | CVSS2 7.5 (High) (AV:N/AC:L/Au:N/C:P/I:P/A:P) | ||||
| CVE-1999-0517 | CVSS2 7.5 (High) (AV:N/AC:L/Au:N/C:P/I:P/A:P) | ||||
| CVE-2004-0311 | CVSS2 10.0 (High) (AV:N/AC:L/Au:N/C:C/I:C/A:C) | ||||
| CVE-2004-1474 | CVSS2 5.0 (Medium) (AV:N/AC:L/Au:N/C:N/I:P/A:N) | ||||
| CVE-2010-1574 | CVSS2 10.0 (High) (AV:N/AC:L/Au:N/C:C/I:C/A:C) | ||||
| First Found | 13 July 2014 | Port | 161/tcp | Last 6 Assessments | 





|
| Vulnerability | 10815 | Cross-Site Scripting

|
Medium Risk |
|---|
| Description | This system is running a web server or web application which is vulnerable to Cross-Site Scripting (XSS) attacks. Certain pages include user-supplied input in the response and HTML special characters are not escaped. An attacker could use this to inject malicious JavaScript or HTML code, which will run at the same trust level as the server. This may enable them to steal session cookies, form details, etc. An example that demonstrates this is: http://www.your_company.nl/tightcms/login.aspx?lang="><img src="" onerror="alert(/Vulnerable/.source)" /> Note: This vulnerability must be addressed server-side. Adding JavaScript (client-side) validation on form fields does not offer any protection against Cross-Site Scripting or other attacks. |
||||
|---|---|---|---|---|---|
| Solution | Recode your web application to ensure all user supplied input is escaped when displayed, or contact your web application vendor for a patch. Any JavaScript-based fix will not be effective. | ||||
| Category | Application or content flaw. | ||||
| References | How To: Prevent Cross-Site Scripting in ASP.NET OWASP XSS Prevention Cheat Sheet PHP htmlspecialchars Quoting Function CERT Advisory CA-2000-02 XSS Anatomy | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 4.3 (Medium) (AV:N/AC:M/Au:N/C:N/I:P/A:N) | |||
| First Found | 13 April 2015 | Port | 80/tcp | Last 6 Assessments | 





|
| Vulnerability | 10539 | Globally Useable Name Server | Medium Risk |
|---|
| Description | This system is running a name server that allows any system on the Internet to perform recursive queries and resolve third-party domain names. An attacker could use this to extract information about your name lookup patterns, and may be able to perform DNS cache poisoning attacks. | ||||
|---|---|---|---|---|---|
| Solution | Restrict recursive queries to trusted addresses. For servers running BIND, use the allow-recursion or allow-query directives. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| References | Disabling recursion in BIND Securing Windows Server 2003 Domain Controllers | ||||
| CVE Reference | CVE-1999-0024 | CVSS2 5.0 (Medium) (AV:N/AC:L/Au:N/C:N/I:P/A:N) | |||
| First Found | 13 March 2015 | Port | 53/udp | Last 6 Assessments | 





|
| Vulnerability | 10991 | IIS global.asa Accessible | Medium Risk |
|---|
| Description | This system is running IIS and allows retrieval of the /global.asa file. This is a global configuation file which may contain sensitive information such as database passwords, physical paths and configuration options. This vulnerability may be caused by a missing ISAPI map of the .asa extension to asp.dll. Here is a sample of your global.asa file: vti_encoding:SR|utf8-nl RealmName:fteap-gtrrss03a InheritPermissions:false PasswordDir:D:\\inetpub\\wwwroot\\huy\\_vti_pvt |
||||
|---|---|---|---|---|---|
| Solution | Restore the .asa map. Alternatively, use a filter program such as URLScan to explicity forbid such requests. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 5.0 (Medium) (AV:N/AC:L/Au:N/C:P/I:N/A:N) | |||
| First Found | 13 March 2015 | Port | 80/tcp | Last 6 Assessments | 





|
| Vulnerability | 10661 | IIS .printer ISAPI Filter Enabled | Medium Risk |
|---|
| Description | This system is running IIS and has the .printer ISAPI filter enabled. Some versions of this filter contain a buffer overrun vulnerability. A remote attacker could use this to crash the service or take control of the system. Note: To avoid crashing your server, we have not directly tested for the vulnerability and this may not be a real hole. However, as the filter is not usually required, you should turn it off as a matter of good practice. |
||||
|---|---|---|---|---|---|
| Solution | If you don't require this filter, disable it. If it is required, make sure the latest patches are applied. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| References | Microsoft Security Bulletin MS01-023 | ||||
| CVE Reference | CVE-2001-0241 | CVSS2 10.0 (High) (AV:N/AC:L/Au:N/C:C/I:C/A:C) | |||
| First Found | 13 February 2015 | Port | 80/tcp | Last 6 Assessments | 





|
| Vulnerability | 90110 | Weak or Ineffective Authentication Mechanism

|
Medium Risk |
|---|
| Description | The remote server attempts to protect content through a mechanism which is ineffective, or can be trivially circumvented. The issue can be demonstrated as follows:The following script appears to form part of the extranet_global application which is password protected. However, http://www.your_company.nl/extranet_global/forms.asp can be accessed without any authentication. |
||||
|---|---|---|---|---|---|
| Solution | Recode your application to use a stronger authentication mechanism. | ||||
| Category | Application or content flaw. | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 6.4 (Medium) (AV:N/AC:L/Au:N/C:P/I:P/A:N) | |||
| First Found | 13 April 2015 | Port | 80/tcp | Last 6 Assessments | 





|
| Vulnerability | 12217 | DNS Cache Snooping | Low Risk |
|---|
| Description | This system is running a DNS server that accepts queries from any address (although recursive queries may be disabled). The name server responds differently for domains that have recently been looked-up. An attacker could use this to determine if certain sites have been visited by users of this nameserver. | ||||
|---|---|---|---|---|---|
| Solution | Restrict access to DNS caches to local users. For Bind, use the "AllowQuery" directive. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| References | What is DNS Cache Snooping? DNS Cache Snooping | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 0.0 (Low) (AV:N/AC:M/Au:N/C:N/I:N/A:N) | |||
| First Found | 13 March 2015 | Port | 53/udp | Last 6 Assessments | 





|
| Vulnerability | 90001 | Holes Detected in Firewall Configuration | Low Risk |
|---|
| Description | This system is protected by a firewall which blocks access to TCP ports in inconsistent ways. Incoming TCP connections to most ports are simply dropped, however some ports were discovered where the connection is actively refused, for example with a TCP RST. This often indicates a firewall configuration error, and commonly occurs when the configuration has not been altered in line with changing system configuration behind the firewall. For example when a service such as a mail server is removed, but the corresponding firewall rule is not. The TCP ports which actively refuse connections are: 81,82 |
||||
|---|---|---|---|---|---|
| Solution | Reconfigure your firewall to completely drop all connections on ports that you are not running services on. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| References | Firewalls FAQ | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 2.6 (Low) (AV:N/AC:H/Au:N/C:P/I:N/A:N) | |||
| First Found | 13 March 2015 | Port | general/tcp | Last 6 Assessments | 





|
| Vulnerability | 10077 | Microsoft Frontpage Extensions Installed | Low Risk |
|---|
| Description | This system is running Microsoft Frontpage extensions. These have had a history of insecurity, so you should carefully check that you have the latest patches applied. It is also common for Frontpage extensions to be insecure because they are misconfigured.Frontpage also reveals the name of the IIS anonymous user IISUSER which could help focus attacks. |
||||
|---|---|---|---|---|---|
| Solution | If you do not require Frontpage extensions, disable them. If they are required, make sure the latest patches are applied. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| References | Microsoft Security Bulletin MS02-018 Microsoft Knowledge Base Q813380 Microsoft Knowledge Base Q813379 | ||||
| CVE Reference | CVE-2000-0114 | CVSS2 5.0 (Medium) (AV:N/AC:L/Au:N/C:P/I:N/A:N) | |||
| First Found | 13 May 2014 | Port | No information available | Last 6 Assessments | 





|
Vulnerabilities Fixed Since the Last Scan: 1 (High:0 Medium:0 Low:1)
| Vulnerability | 10759 | Private IP Address Leakage | Low Risk |
|---|
| Description | This system exposes its RFC 1918 private IP address. This is the internal IP address of the system, that would usually be masked by a proxy or NAT firewall. This information may be useful to an attacker trying to remotely map your network or prepare an attack. The private IP address is:172.258.236.2 |
||||
|---|---|---|---|---|---|
| Solution | Update your web server configuration. For IIS, issue "adsutil set w3svc/UseHostName True" and restart. On Apache, ensure that ServerName in httpd.conf is set to a hostname. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| References | Bugtraq ID 1499 Microsoft Knowledge Base Q218180 RFC 1918 | ||||
| CVE Reference | CVE-2000-0649 | CVSS2 2.6 (Low) (AV:N/AC:H/Au:N/C:P/I:N/A:N) | |||
| First Found | 13 March 2015 | Port | 443/tcp | Last 6 Assessments | 





|
Historical Information