Criticality: 

| Groups and Contacts | |||
|---|---|---|---|
| Region | Asia | Business | janebloggs@yourcompany.com |
| Platform | Unix | Technical | joe.bloggs@technicians.com |
 Scan Information
Scan Information
|
|
|---|---|
| Scan Type | Enterprise |
| Started at | 13-Apr-15 11:54 |
| Finished at | 13-Apr-15 12:54 |
Ports: 3 (High:0 Low:3)
| Port | Protocol | Service | Details | ||
|---|---|---|---|---|---|
| 21 | tcp | ftp | 220 ProFTPD 1.2.1 Server (www.example.com) | ||
| 80 | tcp | http | Apache 1.3.20 Sun Cobalt (Unix) mod_ssl 2.8.4 OpenSSL 0.9.6b PHP 4.3.1 mod_auth_pam_external 0.1 FrontPage 4.0.4.3 mod_perl 1.25 | ||
| 443 | tcp | https | Valid certificate: www.example.com |
Ports Closed Since the Last Scan: 1 (High:0 Low:1)
| Port | Protocol | Service | Details | ||
|---|---|---|---|---|---|
| 3 | icmp | timestamp reply | Timestamp is 12:46:03 |
Vulnerabilities: 11 (High:3 Medium:5 Low:3)
| Vulnerability | 11030 | Apache < 1.3.26 Chunked Encoding Vulnerability | High Risk |
|---|
| Description | This system is running a vulnerable version of Apache, according to its banner. There is a buffer overrun vulnerability in code related to chunked encoding. A remote attacker could use this to crash the service and may be able to take control of the system. | ||||
|---|---|---|---|---|---|
| Solution | Upgrade to an unaffected version, or apply a patch. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| References | CERT Advisory CA-2002-17 US-CERT VU#944335 Apache Security Bulletin 20020620 Bugtraq ID 5033 Apache 1.3 Changelog | ||||
| CVE Reference | CVE-2002-0392 | CVSS2 7.5 (High) (AV:N/AC:L/Au:N/C:P/I:P/A:P) | |||
| First Found | 13 October 2014 | Port | 80/tcp | Last 6 Assessments | 





|
| Vulnerability | 90064 | Authentication Bypass Through Cookie Manipulation

|
High Risk |
|---|
| Description | The remote webserver contains a CGI script or web application which uses cookies for authentication in such a way that login bypass is possible by modifying the cookie value. Example cookie values which allow a login are:By setting the value of the cookie 'USER' to ID=10004&COUNTRY=US&USER_REMEMBER=Y and navigating to http://www.example.com/prizedraw/getuserdata_xml.do we could access the following sensitive information: Name: Jemma Green, DOB: Female 11/9/1976, Password: s3c4r3t, Email: greenj@anymail.com, address details, etc. |
||||
|---|---|---|---|---|---|
| Solution | Recode your web application source code to use stronger authentication. | ||||
| Category | Application or content flaw. | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 6.8 (Medium) (AV:N/AC:M/Au:N/C:P/I:P/A:N) | |||
| First Found | 13 April 2015 | Port | 80/tcp | Last 6 Assessments | 





|
| Vulnerability | 90085 | Sensitive Information Leakage

|
High Risk |
|---|
| Description | This host is leaking information that may be commercially sensitive or help an attacker craft an attack. An example of the information leaked can be found below: The remote AMF gateway application http://www.example.com/messaging/gateway allows unrestricted access to customer ordering information and payment details. For example, calls to com.messaging.partners.getPayment(1337) return the details of the following account. ACCOUNT: 123-123 1234567, CLIENT: Widget Co Ltd, 99 Corked Road, Atlanta AMOUNT: -9845.87 USD ORDERID: 1337 AUTHORISATION_CODE: 1234565 |
||||
|---|---|---|---|---|---|
| Solution | Use a firewall to restrict access to this service. | ||||
| Category | Application or content flaw. | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 5.0 (Medium) (AV:N/AC:L/Au:N/C:P/I:N/A:N) | |||
| First Found | 13 April 2015 | Port | 443/tcp | Last 6 Assessments | 





|
| Vulnerability | 11039 | Apache mod_ssl < 2.8.10 off by one Vulnerability | Medium Risk |
|---|
| Description | This system is running a vulnerable version of the mod_ssl Apache module. There is an "off by one" buffer overrun in code related to parsing configuration. A local user with control over .htaccess files could use this to crash the service or take control of the system. | ||||
|---|---|---|---|---|---|
| Solution | Upgrade to an unaffected version, or apply a patch. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| References | Bugtraq ID 5084 Securiteam advisory | ||||
| CVE Reference | CVE-2002-0653 | CVSS2 4.6 (Medium) (AV:L/AC:L/Au:N/C:P/I:P/A:P) | |||
| First Found | 13 October 2014 | Port | 80/tcp | Last 6 Assessments | 





|
| Vulnerability | 11137 | Apache < 1.3.27 Multiple Vulnerabilities | Medium Risk |
|---|
| Description | This system is running a vulnerable version of Apache, according to its banner. There is a cross-site scripting vulnerability through the Host: header, if UseCanonicalName is Off. Exploitation is only possible where wildcard DNS is used. There is also a buffer overrun in the ApacheBench module - if this is enabled, it may allow arbitrary code execution. A further vulnerability exists in the shared memory scoreboard, but this is only exploitable by a local user. | ||||
|---|---|---|---|---|---|
| Solution | Upgrade to an unaffected version, or apply a patch. Workaround : Set UseCanonicalName to On and disable ApacheBench |
||||
| Category | Hosting or infrastructure flaw. | ||||
| References | Apache 1.3 Changelog | ||||
| CVE References | CVE-2002-0839 | CVSS2 7.2 (High) (AV:L/AC:L/Au:N/C:C/I:C/A:C) | |||
| CVE-2002-0840 | CVSS2 6.8 (Medium) (AV:N/AC:M/Au:N/C:P/I:P/A:P) | ||||
| CVE-2002-0843 | CVSS2 7.5 (High) (AV:N/AC:L/Au:N/C:P/I:P/A:P) | ||||
| First Found | 13 October 2014 | Port | No information available | Last 6 Assessments | 





|
| Vulnerability | 12280 | Apache < 1.3.31, 2.0.49 Multiple Vulnerabilities | Medium Risk |
|---|
| Description | This system is running a vulnerable version of Apache HTTP Server, according to its banner or fingerprint. It is possible for remote attackers to inject escape characters in the log files. A remote attacker can also cause a denial of service by making a long-lasting connection to a rarely used port. For Apache 1.x on 64-bit platforms, there is a mod_access weakness related to IP address rules without a netmask. | ||||
|---|---|---|---|---|---|
| Solution | Upgrade to an unaffected version, or apply a patch. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| References | Buqtraq_9921 Apache 2.0 Changelog Buqtraq ID 9829 Buqtraq ID 9930 US-CERT VU#132110 Apache 1.3 Changelog | ||||
| CVE References | CVE-2003-0020 | CVSS2 5.0 (Medium) (AV:N/AC:L/Au:N/C:N/I:P/A:N) | |||
| CVE-2003-0993 | CVSS2 7.5 (High) (AV:N/AC:L/Au:N/C:P/I:P/A:P) | ||||
| CVE-2004-0174 | CVSS2 5.0 (Medium) (AV:N/AC:L/Au:N/C:N/I:N/A:P) | ||||
| First Found | 13 February 2015 | Port | 80/tcp | Last 6 Assessments | 





|
| Vulnerability | 90068 | SSL Certificate Problems

|
Medium Risk |
|---|
| Description | This system has presented a certificate that does not meet the requirements for establishing a secure session. The problems detected were:
|
||||
|---|---|---|---|---|---|
| Solution | Ensure you have a valid certificate issued by a trusted certificate authority. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| References | Wildcard Certificates X.509 Public Key Certificates Certificate Authorities | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 4.3 (Medium) (AV:N/AC:M/Au:N/C:P/I:N/A:N) | |||
| First Found | 13 April 2015 | Port | 443/tcp | Last 6 Assessments | 





|
| Vulnerability | 90091 | XPath Injection

|
Medium Risk |
|---|
| Description | One or more scripts on this host appear vulnerable to XPath injection attacks. By requesting a page with parameters containing particular XPath elements, it is possible to force an XPath error or otherwise demonstrate that the user supplied code is being interpreted as XPath statements. This implies that a parameter is being passed to an XPath interpreter without proper input validation. A maliciously crafted parameter might be able to extract hidden information, bypass login requirements or even perform code execution depending on the XPath parser used. The issue can be demonstrated as follows: The first URL below returns product information whilst the second does not. This indicates that the injected expressions are being evaluated by an XPath interpreter. http://www.example.com/productcatalog/product.do?id=12 and count(/..)=0 and 1=1 http://www.example.com/productcatalog/product.do?id=12 and count(/..)=0 and 1=0 This is simply an example that illustrates the problem, you should fix the underlying injection issue rather than attempting to prevent this exploit from working. |
||||
|---|---|---|---|---|---|
| Solution | Perform input validation within the web application and utilise query parameterisation where supported by the XPath parser. | ||||
| Category | Application or content flaw. | ||||
| References | XPath Injection - Threat Classification | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 6.8 (Medium) (AV:N/AC:M/Au:N/C:P/I:P/A:P) | |||
| First Found | 13 April 2015 | Port | 80/tcp | Last 6 Assessments | 





|
| Vulnerability | 11915 | Apache < 1.3.29 Multiple Local Flaws | Low Risk |
|---|
| Description | This system is running a vulnerable version of Apache, according to its banner. This version contains buffer overruns in mod_alias and mod_rewrite. A local user could exploit these to escalate their privileges. | ||||
|---|---|---|---|---|---|
| Solution | Upgrade to an unaffected version, or apply a patch. | ||||
| References | Bugtraq Apache 1.3 Changelog | ||||
| CVE Reference | CVE-2003-0542 | CVSS2 7.2 (High) (AV:L/AC:L/Au:N/C:C/I:C/A:C) | |||
| First Found | 13 January 2015 | Port | 80/tcp | Last 6 Assessments | 





|
| Vulnerability | 90001 | Holes Detected in Firewall Configuration | Low Risk |
|---|
| Description | This system is protected by a firewall which blocks access to TCP ports in inconsistent ways. Incoming TCP connections to most ports are simply dropped, however some ports were discovered where the connection is actively refused, for example with a TCP RST. This often indicates a firewall configuration error, and commonly occurs when the configuration has not been altered in line with changing system configuration behind the firewall. For example when a service such as a mail server is removed, but the corresponding firewall rule is not. The TCP ports which actively refuse connections are: 25 |
||||
|---|---|---|---|---|---|
| Solution | Reconfigure your firewall to completely drop all connections on ports that you are not running services on. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| References | Firewalls FAQ | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 2.6 (Low) (AV:N/AC:H/Au:N/C:P/I:N/A:N) | |||
| First Found | 13 November 2014 | Port | general/tcp | Last 6 Assessments | 





|
| Vulnerability | 11213 | TRACE and/or TRACK Methods Enabled | Low Risk |
|---|
| Description | This system supports the HTTP TRACE and/or TRACK methods. These increase the exploitability of any cross-site scripting vulnerabilities that may exist in your site. As they are primarily intended for debugging, they can be turned off without reduction of service. | ||||
|---|---|---|---|---|---|
| Solution | Disable these methods on production servers. Microsoft IIS 6 and IIS 7: Use the URLScan Security tool Microsoft IIS 5: Use the IIS Lockdown tool Apache httpd: Use mod_rewrite to redirect unallowed verbs to the forbidden target, or with newer versions use the configuration option 'TraceEnable off'. |
||||
| Category | Hosting or infrastructure flaw. | ||||
| References | US-CERT VU#867593 UrlScan Security Tool IIS Lockdown Tool Apache TraceEnable Directive | ||||
| CVE References | CVE-2003-1567 | CVSS2 2.6 (Low) (AV:N/AC:H/Au:N/C:P/I:N/A:N) | |||
| CVE-2004-2320 | CVSS2 2.6 (Low) (AV:N/AC:H/Au:N/C:P/I:N/A:N) | ||||
| CVE-2010-0386 | CVSS2 2.6 (Low) (AV:N/AC:H/Au:N/C:P/I:N/A:N) | ||||
| First Found | 13 March 2015 | Port | 80/tcp | Last 6 Assessments | 





|
Vulnerabilities Fixed Since the Last Scan: 1 (High:0 Medium:0 Low:1)
| Vulnerability | 10114 | ICMP Timestamp Request | Low Risk |
|---|
| Description | This system responds to ICMP timestamp requests. A remote attacker could use such requests to determine the exact date and time on the system. This information could be used in attacks against time-based authentication protocols. | ||||
|---|---|---|---|---|---|
| Solution | Either disable timestamp replies, or filter them at your firewall. | ||||
| CVE Reference | CVE-1999-0524 | CVSS2 0.0 (Low) (AV:L/AC:L/Au:N/C:N/I:N/A:N) | |||
| First Found | 13 March 2015 | Port | No information available | Last 6 Assessments | 





|
Historical Information
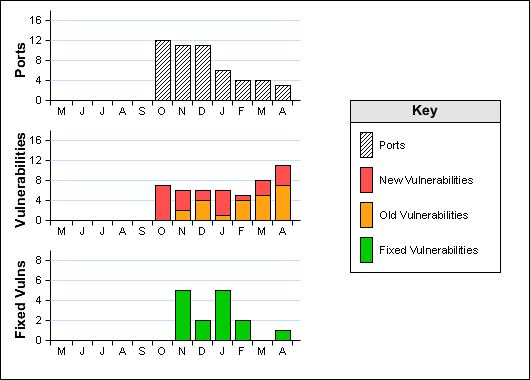
Stoplisted Vulnerabilities for this Host: 2
| Vulnerability | 12085 | Apache Tomcat Servlet / JSP Container Default Files | Low Risk |
|---|
| Description | This system is running an Apache Tomcat servlet/JSP container with default files (such as documentation, default Servlets and JSPs) installed. These files may help an attacker to guess the exact version of the Apache Tomcat which is running on this host and may provide other useful information. | ||||
|---|---|---|---|---|---|
| Solution | Remove default files, example JSPs and Servlets from the Tomcat Servlet/JSP container. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| References | Apache Tomcat Home Page | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 0.0 (Low) (AV:N/AC:L/Au:N/C:N/I:N/A:N) | |||
| First Found | 13 March 2015 | Port | 443/tcp | Last 6 Assessments | 





|
| Stopped | By: joe.bloggs@technicians.com From: 12 March 2003 To: 12 March 2018 | ||||
| Reason | Your Company accepts the risk that this vulnerability poses. | ||||
| Vulnerability | 11046 | Apache Tomcat TroubleShooter Servlet Detected | Low Risk |
|---|
| Description | The remote Apache Tomcat server has the TroubleShooter servlet accessible. This displays information about your system configuration, which may be useful to attackers. It can also be used to perform cross-site scripting attacks. You can access the servlet through this URL: https://192.168.0.112/examples/servlet/TroubleShooter
|
||||
|---|---|---|---|---|---|
| Solution | Remove the example files from production servers. If you do require this functionality, protect it using password or IP address authentication. | ||||
| CVE Reference | CVE-2002-2006 | CVSS2 5.0 (Medium) (AV:N/AC:L/Au:N/C:P/I:N/A:N) | |||
| First Found | 13 March 2015 | Port | 443/tcp | Last 6 Assessments | 





|
| Stopped | By: joe.bloggs@technicians.com From: 12 March 2003 To: 12 March 2018 | ||||
| Reason | Your Company accepts the risk that this vulnerability poses. | ||||