Criticality: 

| Groups and Contacts | |||
|---|---|---|---|
| Region | Asia | Business | janebloggs@yourcompany.com |
| Platform | Microsoft | Business | manager@yourcompany.com |
| Technical | joe.bloggs@technicians.com | ||
| Technical | johndoe@yoursecurity.co.uk | ||
 Scan Information
Scan Information
|
|
|---|---|
| Scan Type | Enterprise |
| Started at | 13-Apr-15 11:54 |
| Finished at | 13-Apr-15 12:54 |
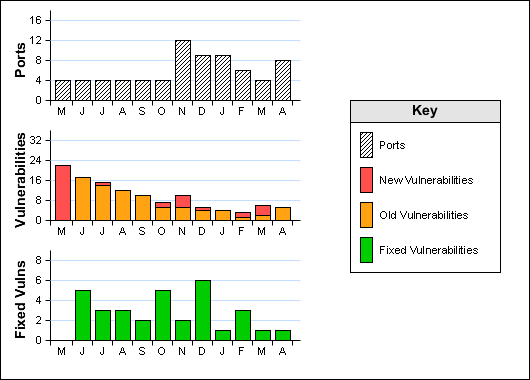
Ports: 8 (High:0 Low:8)
| Port | Protocol | Service | Details | ||
|---|---|---|---|---|---|
| 22 | tcp | ssh | SSH-1.99-OpenSSH_3.4p1 | ||
| 25 | tcp | smtp | 220 mail.example.com ESMTP Sendmail 8.10.2 8.10.2 Sat, 13 Apr 2015 12:09:09 +0100 | ||
| 110 | tcp | pop3 | +OK Qpopper (version 4.0.4) at mail.example.com starting. | ||
| 143 | tcp | imap | * OK [CAPABILITY IMAP4REV1 LOGIN-REFERRALS STARTTLS AUTH=LOGIN] mail.example.com IMAP4rev1 2001.315 at Sat, 13 Apr 2015 12:09:05 +0100 (BST) | ||

|
0 | icmp | echo reply | Response Received | |

|
3.3 | icmp | port unreachable | Response Received | |

|
3.2 | icmp | protocol unreachable | Response Received | |

|
14 | icmp | timestamp reply | Timestamp is 12:51:58 (Windows style) |
Vulnerabilities: 5 (High:2 Medium:2 Low:1)
| Vulnerability | 11316 | Sendmail < 8.12.8 Buffer Overrun

|
High Risk |
|---|
| Description | This system is running a vulnerable version of Sendmail, according to its banner. There is a buffer overrun vulnerability in code related to message header parsing. A remote attacker could use this to crash the service or possibly take control of the system. This version may also be vulnerable to a flaw in smrsh which allows local users to escalate their privileges. | ||||
|---|---|---|---|---|---|
| Solution | Upgrade to an unaffected version, or apply a patch. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| References | US-CERT VU#398025 | ||||
| CVE References | CVE-2001-1349 | CVSS2 3.7 (Low) (AV:L/AC:H/Au:N/C:P/I:P/A:P) | |||
| CVE-2002-1165 | CVSS2 4.6 (Medium) (AV:L/AC:L/Au:N/C:P/I:P/A:P) | ||||
| CVE-2002-1337 | CVSS2 10.0 (High) (AV:N/AC:L/Au:N/C:C/I:C/A:C) | ||||
| Deadline | 01 May 2015 | ||||
| First Found | 13 May 2014 | Port | 25/tcp | Last 6 Assessments | 





|
| Vulnerability | 10882 | SSH Protocol Version 1 Enabled | High Risk |
|---|
| Description | This system is running an SSH service with SSH protocol version 1 enabled. This version of the protocols is not completely cryptographically secure. A passive eavesdropper could use these weaknesses to extract information such as the lengths of passwords and commands. | ||||
|---|---|---|---|---|---|
| Solution | Configure your SSH service to only use protocol version 2. For OpenSSH, set the 'Protocol' option to '2'. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| References | US-CERT VU#596827 OSVDB ID 2116 | ||||
| CVE References | CVE-2001-0361 | CVSS2 4.0 (Medium) (AV:N/AC:H/Au:N/C:P/I:P/A:N) | |||
| CVE-2001-0572 | CVSS2 7.5 (High) (AV:N/AC:L/Au:N/C:P/I:P/A:P) | ||||
| CVE-2001-1473 | CVSS2 7.5 (High) (AV:N/AC:L/Au:N/C:P/I:P/A:P) | ||||
| First Found | 13 November 2014 | Port | 22/tcp | Last 6 Assessments | 





|
| Vulnerability | 11574 | OpenSSH < 3.6.1p2 PAM Timing Attack | Medium Risk |
|---|
| Description | This system appears to be running a vulnerable version of OpenSSH. If PAM authentication is used there is a timing attack against the protocol. A remote attacker could use this to conduct brute force attacks against users' passwords. Note: Tests for this vulnerability are sensitive to network conditions. This vulnerability may be a false positive. |
||||
|---|---|---|---|---|---|
| Solution | Upgrade to an unaffected version, or apply a patch. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| CVE References | CVE-2003-0190 | CVSS2 5.0 (Medium) (AV:N/AC:L/Au:N/C:P/I:N/A:N) | |||
| CVE-2003-1562 | CVSS2 5.1 (Medium) (AV:N/AC:H/Au:N/C:P/I:P/A:P) | ||||
| First Found | 13 March 2015 | Port | 22/tcp | Last 6 Assessments | 





|
| Vulnerability | 10249 | SMTP Server Allows VRFY/EXPN | Medium Risk |
|---|
| Description | This system is running an SMTP server which allows the VRFY and/or EXPN commands. These can be used to check the validity of accounts, find the delivery address of mail aliases, or even determine the full name of a recipient. An attacker could use this information to focus their attacks, or aid social engineering. The information leakage is unnecessary so you should disable these commands. | ||||
|---|---|---|---|---|---|
| Solution | If you are using sendmail, add the configuration directive 'PrivacyOptions=goaway'. For other mail daemons, consult the documentation. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| References | RFC 2505 The VRFY and EXPN verbs | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 5.0 (Medium) (AV:N/AC:L/Au:N/C:P/I:N/A:N) | |||
| First Found | 13 March 2015 | Port | 25/tcp | Last 6 Assessments | 





|
| Vulnerability | 90001 | Holes Detected in Firewall Configuration | Low Risk |
|---|
| Description | This system is protected by a firewall which blocks access to TCP ports in inconsistent ways. Incoming TCP connections to most ports are simply dropped, however some ports were discovered where the connection is actively refused, for example with a TCP RST. This often indicates a firewall configuration error, and commonly occurs when the configuration has not been altered in line with changing system configuration behind the firewall. For example when a service such as a mail server is removed, but the corresponding firewall rule is not. The TCP ports which actively refuse connections are: 80,443 |
||||
|---|---|---|---|---|---|
| Solution | Reconfigure your firewall to completely drop all connections on ports that you are not running services on. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| References | Firewalls FAQ | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 2.6 (Low) (AV:N/AC:H/Au:N/C:P/I:N/A:N) | |||
| First Found | 13 March 2015 | Port | general/tcp | Last 6 Assessments | 





|
Vulnerabilities Fixed Since the Last Scan: 1 (High:0 Medium:1 Low:0)
| Vulnerability | 10965 | SSH 3 AllowedAuthentication | Medium Risk |
|---|
| Description | According to its banner, the remote server is running a version of SSH which is between 3.0.0 and 3.1.2. There is a vulnerability in this release that may, under some circumstances, allow users to authenticate using a password whereas it is not explicitely listed as a valid authentication mecanism. An attacker may use this flaw to attempt to brute force a password using a dictionnary attack (if the passwords used are weak). | ||||
|---|---|---|---|---|---|
| Solution | Upgrade to version 3.1.2 of SSH which solves this problem. | ||||
| References | Bugtraq ID 4810 | ||||
| CVE References | CVE-2002-1646 | CVSS2 7.5 (High) (AV:N/AC:L/Au:N/C:P/I:P/A:P) | |||
| CVE-2005-0962 | CVSS2 7.5 (High) (AV:N/AC:L/Au:N/C:P/I:P/A:P) | ||||
| First Found | 13 March 2015 | Port | No information available | Last 6 Assessments | 





|
Historical Information