Criticality:  System Reference: YC105
System Reference: YC105
 System Reference: YC105
System Reference: YC105
| Groups and Contacts | |||
|---|---|---|---|
| Region | EMEA | Business | janebloggs@yourcompany.com |
| Platform | Other | Technical | joe.bloggs@technicians.com |
 Scan Information
Scan Information
|
|
|---|---|
| Scan Type | Enterprise |
| Started at | 13-Apr-15 11:54 |
| Finished at | 13-Apr-15 12:54 |
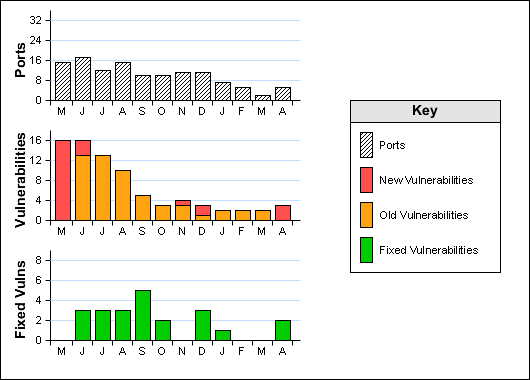
Ports: 5 (High:3 Low:2)
| Port | Protocol | Service | Details | ||
|---|---|---|---|---|---|

|
23 | tcp | telnet | User Access Verification | |

|
53 | tcp | domain | None | |

|
53 | udp | dns | version.bind TXT "8.3.3-REL" | |

|
69 | udp | tftp | Server Found, Error (You are not unlocked for reading) | |

|
161 | udp | snmp | uptime 272559693 centiseconds |
Ports Closed Since the Last Scan: 2 (High:0 Low:2)
| Port | Protocol | Service | Details | ||
|---|---|---|---|---|---|
| 113 | tcp | auth | Response Received | ||
| 750 | tcp | kerberos | No banner found |
Vulnerabilities: 3 (High:2 Medium:1 Low:0)
| Vulnerability | 90027 | High Risk Ports Open

|
High Risk |
|---|
| Description | The following high risk ports are open: PORT SERVICE 23/tcp telnet 69/udp tftp 161/udp snmp Note: Even if the ports are immediately closed after being opened, this is still a security risk as packets are reaching the destination host. It is recommended to completely drop packets from untrusted sources instead. |
||||
|---|---|---|---|---|---|
| Solution | Ensure that the ports are filtered by your router or firewall or close the ports on the affected systems. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| CVE Reference | CVE-MAP-NOMATCH | CVSS2 6.4 (Medium) (AV:N/AC:L/Au:N/C:P/I:P/A:N) | |||
| First Found | 13 May 2014 | Port | general | Last 6 Assessments | 





|
| Vulnerability | 10264 | SNMP Default Community Names

|
High Risk |
|---|
| Description | This system is running an SNMP agent which uses an easily guessable community string. This enables an attacker to extract a large amount of useful information. If a writeable community string is guessable, an attacker could make configuration changes to the server. Here is a sample of the information that can be extracted: host.hrSWRun.hrSWRunTable.hrSWRunEntry.hrSWRunName.168 = "SMSS.EXE" host.hrSWRun.hrSWRunTable.hrSWRunEntry.hrSWRunName.192 = "CSRSS.EXE" host.hrSWRun.hrSWRunTable.hrSWRunEntry.hrSWRunName.212 = "WINLOGON.EXE" |
||||
|---|---|---|---|---|---|
| Solution | Disable SNMP, or change the community string to something unguessable. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| CVE References | CVE-1999-0186 | CVSS2 10.0 (High) (AV:N/AC:L/Au:N/C:C/I:C/A:C) | |||
| CVE-1999-0254 | CVSS2 10.0 (High) (AV:N/AC:L/Au:N/C:C/I:C/A:C) | ||||
| CVE-1999-0516 | CVSS2 7.5 (High) (AV:N/AC:L/Au:N/C:P/I:P/A:P) | ||||
| CVE-1999-0517 | CVSS2 7.5 (High) (AV:N/AC:L/Au:N/C:P/I:P/A:P) | ||||
| CVE-2004-0311 | CVSS2 10.0 (High) (AV:N/AC:L/Au:N/C:C/I:C/A:C) | ||||
| CVE-2004-1474 | CVSS2 5.0 (Medium) (AV:N/AC:L/Au:N/C:N/I:P/A:N) | ||||
| CVE-2010-1574 | CVSS2 10.0 (High) (AV:N/AC:L/Au:N/C:C/I:C/A:C) | ||||
| First Found | 13 April 2015 | Port | 161/udp | Last 6 Assessments | 





|
| Vulnerability | 10539 | Globally Useable Name Server

|
Medium Risk |
|---|
| Description | This system is running a name server that allows any system on the Internet to perform recursive queries and resolve third-party domain names. An attacker could use this to extract information about your name lookup patterns, and may be able to perform DNS cache poisoning attacks. | ||||
|---|---|---|---|---|---|
| Solution | Restrict recursive queries to trusted addresses. For servers running BIND, use the allow-recursion or allow-query directives. | ||||
| Category | Hosting or infrastructure flaw. | ||||
| References | Disabling recursion in BIND Securing Windows Server 2003 Domain Controllers | ||||
| CVE Reference | CVE-1999-0024 | CVSS2 5.0 (Medium) (AV:N/AC:L/Au:N/C:N/I:P/A:N) | |||
| First Found | 13 May 2014 | Port | 53/udp | Last 6 Assessments | 





|
Vulnerabilities Fixed Since the Last Scan: 2 (High:0 Medium:0 Low:2)
| Vulnerability | 10021 | Identd enabled | Low Risk |
|---|
| Description | The ident service appears to be running on the remote host. This service provides sensitive information to an attacker, allowing them to enumerate which accounts are running which services. | ||||
|---|---|---|---|---|---|
| Solution | Disable this service or restrict it to trusted IP addresses | ||||
| CVE Reference | CVE-1999-0629 | CVSS2 0.0 (Low) (AV:N/AC:L/Au:N/C:N/I:N/A:N) | |||
| First Found | 13 May 2014 | Port | 113/tcp | Last 6 Assessments | 





|
| Vulnerability | 10640 | Kerberos PingPong DOS | Low Risk |
|---|
| Description | The remote kerberos server seems to be vulnerable to a pingpong attack. When contacted on the UDP port, this service always responds, even to bogus data. An attacker can cause a denial of service attack, by spoofing a packet between two machines running this service. This will cause them to spew data at each other, saturating the network. | ||||
|---|---|---|---|---|---|
| Solution | Disable this service in /etc/inetd.conf. | ||||
| CVE Reference | CVE-1999-0103 | CVSS2 5.0 (Medium) (AV:N/AC:L/Au:N/C:N/I:N/A:P) | |||
| First Found | 13 December 2014 | Port | 750/tcp | Last 6 Assessments | 





|
Historical Information